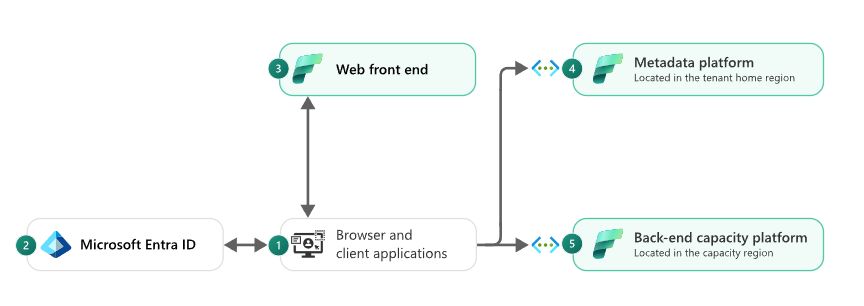
User Access and Interaction:
- Imagine a user sitting at their computer or mobile device, opening a browser or using a client application like Power BI Desktop. The user wants to access the Fabric service to view, analyze, or work on their data. The first step is connecting to the Fabric service, which is hosted in the cloud.
Authentication and Identity Management:
- Before the user can actually access any resources or data, their identity needs to be verified. This is where Microsoft Entra ID comes into play (formerly known as Azure Active Directory). Microsoft Entra ID is the service responsible for checking the user’s credentials (like their username and password) and confirming whether they are allowed to access the service. This step ensures that only legitimate users or service accounts can interact with the Fabric service.
Handling User Requests at the Web Front End:
- Once the user is authenticated, their request is processed by the web front end of the Fabric service. This is like a gateway that receives the user’s requests, manages their login, and ensures they get to the right place. The web front end also routes the requests to the appropriate components and serves content (like dashboards or reports) back to the user.
Managing Metadata and Authorization:
- In the background, there’s a metadata platform that stores important information about each customer’s environment (called tenant metadata). This metadata can include things like data about the organization’s users, their permissions, and other configuration details. Whenever a service needs to know if a user is allowed to do something, it queries this metadata platform to get that information. This platform is located in the tenant’s home region, which is a specific geographic area where their data is managed.
Back-End Capacity Platform:
- The heavy lifting, such as processing data and storing it, happens in the back-end capacity platform. This platform is responsible for the compute operations and storage of customer data. It is strategically located in a region where the organization has purchased capacity. The back-end platform relies on Azure core services to provide specific Fabric experiences, like data analysis or visualization.
Secured Virtual Networks and Internet Protection:
- Both the metadata platform and the back-end capacity platform operate within secured virtual networks. These are protected, isolated networks that are designed to keep the data and operations safe. Although these networks do expose secure endpoints (access points) to the internet so that customers and other services can interact with them, they are carefully protected. The public cannot access the underlying services directly because they are shielded by strict network security rules. These rules block any unauthorized attempts from the internet.
Restricted Internal Communication:
- Even within these secure virtual networks, not all services can talk to each other freely. The communication is restricted and tightly controlled based on the specific roles and privileges assigned to each service. This minimizes the risk of unauthorized access even within the internal environment.